#proxy software
Explore tagged Tumblr posts
Text

Research for Gaza & Sudan
Hello everyone, this is my attempt in helping Raise funds for 3 campaigns that are in dire need and are extremely low on funds.
What I can do:
I am a physics major & have access to neat software such as HyperChem & Gaussian 09 and know how to use both efficiently. I can help build & do the necessary calculations for your modules. I can help you find resources for your research, and I am open to doing math and/or physics homework, as well.
How does this work?
DM me your requirements WITH CLEAR INSTRUCTIONS & a screenshot of your donations and I will start on it as soon as I can.
• For HyperChem & Gaussian 09: you need to donate €25 to each of the two gaza campaigns I have below.
I think this is a more than fair price given that licenses for both softwares range from 50$-2500$ (in the academics alone!)
• For searching resources: you need to donate €10 for the Sudanese campaign below.
• For homework: you need to donate €10 to any of the campaigns below.
NOTE: I am NOT responsible for Your deadlines. If your request needs time to run or I am doing someone else's commission before you, you WILL have to wait.
The campaigns:
Al-Najjar family - vetted here
Abdul Aziz's family - vetted here
ThomaSerena - vetted here & here
Sorry for the tags ♡
@commissions4aid-international @northgazaupdates2 @appsa @magnus-rhymes-with-swagness @wingedalpacacupcake @elksewer @a-shade-of-blue @tortiefrancis @mushroomjar @fromjannah @neechees @irhabiya @ibtisams @lacecap @dykesbat @socalgal @ankle-beez @mahoushojoe @transmutationisms @deepspaceboytoy @greelin @huckleberrycomics @zionistsinfilm @beserkerjewel @babacontainsmultitudes @spacebeyonce @mauesartetc @vakarians-babe @ghostofanonpast @c-u-c-koo-4-40k @ot3 @xinakwans @komsomolka @chilewithcarnage @akamanto0 @feluka @goodguydotmp3 @leotanaka @effen-draws @pkmnbutch @bilal-salah0 @ghostingarden
#research#dark academia#academic#academia#physics#math#science#hyperchem#gaussian blur#gaza strip#israel#sudan#sudan war#proxy war#sudan criss#sudan gofundme#evacuation#humanitarian aid#AcePR#chemistry#do your homework#software#gravity falls#Palestine#gaza#free gaza#free palestine
2K notes
·
View notes
Text
#spyware#internet#infotech#it#i.t.#information technology#software#firmware#espionage#online privacy#internet privacy#data privacy#invasion of privacy#privacy#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#class war#earth#oppression#repression#proxy war#eat the rich
25 notes
·
View notes
Text
why's it so hard to set up a custom minecraft server...
#like cmon I have a public facing server already#I know it works since the logs dont show any errors#and like ive tried running the exact same hardware+software setup on my local network#but like unfortunately the public facing server only has IPv6#and I cant connect cause my ISP only issues IPv4#and the other people I want to play with probably only have v4 as well#I guess the hosting provider I have technically has a v4->v6 proxy to allow ppl with v4 only to connect to their servers#but it only passes through http imap and smtp traffic#so its pretty much useless for what I want to do#and like so far finding a proxy service that actually does what i want it to do seems impossible#like PLEASE I WANNA PLAY MINECRAFT WITH SOMEONE ELSE#I DONT WANNA SPEND TIME TRYING TO FIGURE OUT HOW TO GET THE SERVER RUNNING
3 notes
·
View notes
Note
🧠 + go pet the lion at the zoo.
Send 🧠 + an intrusive thought for my muse to have, and they'll react to having it!

The more he thinks about it, the more tempting it becomes, and it's not long before he's debating the methods needed to make it feasible, with himself.
#gotham's proxy guardian#Osprey Answers#//Okay but like#//All cats run the same software so a loooot of catnip
0 notes
Text
0 notes
Text
Purecode | Backend Proxy
Consider making API requests through a backend server where your API key is stored and not exposed to the frontend. This way, the API key is kept hidden from the client-side, reducing the potential for unauthorized access.
#Backend Proxy#Consider making API requests#API key is kept hidden#potential for unauthorized access.#purecode#purecode ai company reviews#purecode ai reviews#purecode company#purecode software reviews#purecode reviews
0 notes
Text
Guide to building Software routers and IP Proxies: Improving the efficiency of network operations
With the growing demand for Internet, the concept of Software router is becoming familiar to the public. For individuals, businesses or technology enthusiasts, Software router not only provides highly flexible network management, but also allows users to realize more complex network operations by configuring Proxies IP. It transforms into a powerful router through a software-defined router system, typically used on low-power computing devices such as a Raspberry Pi or a mini-PC running Linux, with the addition of specific router software (e.g. OpenWRT, LEDE, etc.).
In this article, I'll provide a comprehensive introduction to Software routers, discuss how to improve network efficiency through Soft Routing with Proxies IP, and provide concrete steps to follow.
What is a Software router?
Software routers and hard routes are two common routing methods used in current network architectures. First of all, before we figure out Software router, we need to understand what is hard routing?
What is hard routing?

Introduction to Software router?
From the official definition, Software router is actually a router solution through desktop or server with corresponding software. Users can choose the operating system and hardware devices according to their needs, and can even set up and optimize them to achieve some advanced functions.
Compared to hard routing, Software router is a more flexible and powerful routing solution. The concept of Software router is to use desktops, servers or virtual machines as hardware carriers and utilize a specific software system to realize the routing function. The most important feature of Software router is that its software and hardware are completely independent and separate.

The core components of a Software router include: a system, a network card, and a proxy service or firewall. At least two of these network cards are required, one for connecting to the external network (WAN) and the other for managing the internal network (LAN). Advanced users can also use multiple network ports for features such as broadband aggregation.
What are the advantages of Software router?
Software routers have several significant advantages over hard routes:
Flexibility: Software router does not depend on a specific device and users can choose to run it on any supported device, including desktops, servers, and even virtual machines. By choosing different operating systems and software packages, users can adapt the router's functionality to their needs.
Feature-rich: Software router is not only limited to basic Internet access functions, it can also realize traffic management, QoS (quality of service control), VLAN (virtual LAN) and other advanced functions. Users can customize various routing policies to achieve more complex network management needs.
High scalability: Since Software router relies on software to realize its functions, users can constantly expand its functions by upgrading software or adding plug-ins. For example, adding services such as ad blocking, firewall, Proxies, etc. can be realized by simply installing the corresponding software packages on the Software router.
Hardware selection for Software router
While Software routers are highly flexible, it is also important to choose the right hardware device in order to run stably for a long period of time:
Low Power Consumption: Software router needs to run for a long time, the host with power consumption under 20W is more energy efficient and suitable for long-term use.
Multi-port support: If bandwidth aggregation is required, choose a device with multiple ports to enhance network speed.
Compact size: The device should be small enough to be easily placed in the home or office without taking up space.
USB interface: convenient for external large-capacity hard disk, suitable for home server.
Gigabit/2.5G ports: Prepare for future network upgrades and adapt to higher bandwidth demands.
Construction diagram of a Software router
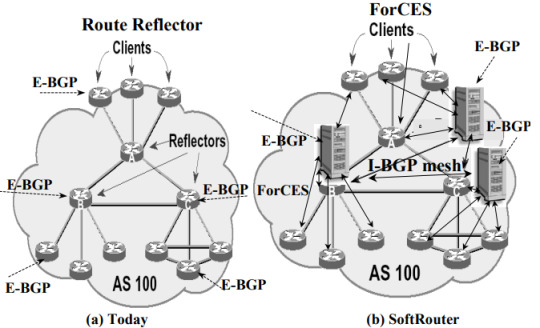
What can I do with a Software router?
With Software router, users can achieve a variety of network functions, it can optimize network performance and traffic management, multiple broadband aggregation, firewall and network security management, advertisement blocking and web filtering, self-built home cloud servers, remote control and monitoring network, Proxies IP setup and management, virtual local area network (VLAN) segmentation, customized routing policies, and so on and so forth.
Especially when used in combination with Proxies IP, it can significantly enhance network flexibility and security. First, Software router enables users to flexibly configure complex network policies, such as traffic management and access control, to ensure rational allocation of network resources. Users can set traffic limits for different devices and optimize bandwidth utilization to ensure smooth operation of critical applications.
With Software routers, users can easily use Proxy IPs to hide their real IP addresses, reducing the risk of being traced, ensuring secure access to websites and avoiding information leakage. In addition, Proxy IPs can also improve access speeds, as Proxy Services can provide faster response times in some cases.
Combined with Proxy IPs, Software router users are able to flexibly configure multiple proxy connections and choose different Proxies to fulfill different usage scenarios, such as Web Crawling, Web Scraping or Market Research. This flexibility enables users to achieve higher efficiency and success rates when dealing with diverse network tasks.
Software routers are also quite scalable, allowing users to enhance the security of their network through plug-ins or additional configurations, such as adding firewalls and intrusion detection systems. Even when using Proxy IP for network activities, users are still able to maintain a high level of security protection and effectively avoid potential Secure Proxy threats. Overall, the combination of Software router and Proxy IP provides users with a more Secure Proxy and efficient Porfiles. Here I focus on how to use Software router to configure Proxies IP.
Proxies IP Introduction
Proxies IPs are intermediate servers that allow users to perform network operations through another IP address. Using Proxies IPs can hide real IP addresses, break through certain geographic restrictions, enhance privacy, and prevent IP blocking by certain websites. There are many types of Proxies, including Static Residential Proxies, Rotating Residential Proxies, and more.
Static Residential IP: unchanged for a long period of time, suitable for operations that require a stable connection.
Rotating Residential IP: The IP address changes periodically, suitable for scenarios that require random IP switching.
Advantages of Software routers with Proxies
When Software router is used in combination with Proxies IP, the flexibility and controllability of network operation will be greatly improved. This combination is suitable for a variety of application scenarios, especially when frequent IP switching or batch network operations are required, and has significant advantages.
1. Fine-grained control of network traffic
Software router allows users to precisely manage and control traffic. By pairing Proxy IPs, users can assign different network requests to different Proxy Services. For example, certain requests can be sent through a residential IP while other sensitive operations are performed through a Rotating IP. This enhances privacy while ensuring the stability of the network connection.
2. Automated Proxies switching
The power of Software router lies in its programmability, which allows users to write scripts or use existing plug-ins to switch Proxies IPs automatically.This is especially important for those who need to operate in bulk or visit multiple websites. For example, by automatically rotating IPs with Software router, you can effectively avoid the same IP being blocked or flagged as abnormal behavior by multiple websites.
3. Enhancing privacy and security
Software router itself can provide additional Secure Proxies through its firewall function, while Proxy IP further enhances network privacy. When combining the two, users can not only hide their real IPs, but also realize multiple levels of Secure Proxies through Proxies Chaining (chained proxies) to prevent traffic from being traced or monitored.
5. Improving marketing and data collection efficiency
In e-commerce, advertising, market research and other scenarios, batch operation is a common demand. With Software router combined with Proxies IP, users can automate data crawling through different IP addresses to avoid being blocked due to excessive access from a single IP address. This approach not only improves operational efficiency, but also significantly reduces the risk of account blocking.
Software router configuration Proxies IP implementations
Step 1: Install the Software router operating system
First, choose a device that can run stably as a Software router server, such as an old computer with strong performance, a mini-server, or a dedicated Software router device (e.g., a host with x86 architecture). Make sure the device has at least two network cards, one connecting to the external network (WAN) and the other for the internal network (LAN).
Download and install the Software router system:
OpenWRT: Lightweight and suitable for a wide range of hardware devices.
pfSense: full-featured and suitable for users who need more advanced features.
MikroTik: Powerful and flexible, but requires a bit of a learning curve.
Take OpenWRTas an example, the download and installation steps are as follows:
Visit the official OpenWRT website to download the image file for your device architecture.
Use a USB utility (e.g. Rufus) to write the image to a USB flash drive, then plug it into the Software router device, go into the BIOS to set up booting from the USB flash drive and install the system.
Basic network configuration:
Enter the Web management interface of the Software router (usually accessed through the intranet IP address, initially set to 192.168.1.1).
Configure the WAN port to connect to the Internet and ensure that the LAN port can assign IP addresses to internal devices.
Verify that the network connection is working properly: use intranet devices to access the Internet and ensure that basic network functions are working well.
Step 2: Configure Proxies IPs
Configuring Proxy IP is the core step to realize the combination of Software router and Proxy service. The following is the detailed Proxies IP configuration process, specifically OpenWRT as an example for illustration, other Software router operating systems such as pfSense and MikroTik operation is similar.
Get Proxy IP service information: Get Proxies information through Proxy IP service provider (e.g. Proxy4Free.com).
Install Proxies Plug-ins (e.g. Shadowsocks, Privoxy, etc.): On the Software router, install the relevant Proxies plug-ins via the package manager (opkg). For example, Shadowsocks can handle multiple Proxies.
Install the Shadowsocks client on OpenWRT:
In the web management interface, go to "System" -> "Software" and click on "Update lists ".
Search for "shadowsocks", select and install the shadowsocks-libev package.
Once the installation is complete, go to "Services" -> "Shadowsocks" and start configuring Proxies.
Configure Proxies IP:
Go to the Shadowsocks configuration page and click "Add new instance".
Basic settings:
Server: Enter the IP address of the Proxies you obtained from your proxy service provider.
Port: Enter the port number provided by the Proxies service provider.
Password: Enter the Proxies account password (if any).
Encryption Method: Select the encryption protocol recommended by the Proxies service provider (usually aes-256-gcm, etc.).
Advanced Settings(optional):
Setting Multi-Proxies Policy: If there are multiple Proxies IPs to choose from, you can assign different Proxies IPs to different devices and applications.
Save and apply the settings.
Configure routing rules:
In the web management interface of Software router, go to "Network" -> "Firewall" -> "Traffic Rules". Rules".
Create a new rule to forward specific traffic (e.g. HTTP, HTTPS traffic) through Proxies IP. Traffic rules can be customized for different device or application types.
If you need to use Proxies for specific external websites or destination IPs, you can set up IP-based routing policies in the Routing section to forward these specific traffic through the Proxy IP.
Verify the Proxies configuration:
After the configuration is complete, open a device connected to the Software router and visit the IP address lookup website to see if the IP currently in use is a Proxies IP.
Check that the Proxy Service is working properly to ensure that traffic is passing through the proxy server correctly.
Step 3: Implement automated switching of Proxies IPs
Sometimes, users may need to switch Proxies IPs automatically, especially for batch operations or to avoid website blocking. Software router supports automated switching of Proxies IP through scripts or plug-ins. Here is how to realize this function in OpenWRT.
Install the cron timed task plugin:
Go to "System" -> "Software" and search for and install the cron plugin.
cron allows you to create timed tasks that can switch Proxies IPs periodically.
Write switching scripts:
Connect to the Software router using SSH and edit the script file (e.g. /etc/proxy-switch.sh) which will operate by modifying the Proxies settings or switching between different Proxies IPs.#!/bin/sh # Switch Proxies IP ifconfig eth0 down # Modify Proxies settings uci set shadowsocks.server='New Proxies IP' uci commit shadowsocks etc/init.d/shadowsocks restart ifconfig eth0 up
Set up timed tasks:
Ensure that Proxies IPs are switched on a regular basis by running scripts on a regular basis via a cron task.
Go to "System" -> "Scheduled Tasks" and add the following timed task
0 * * * * * /etc/proxy-switch.sh
The task will be automatically executed every hour, switching Proxies.
Test automated switching functions:
Wait for the timed task to execute and verify that the Proxies IPs are automatically switched as expected. You can check the current IP address by visiting the IP Lookup website or other extranet services.
Suppose you want to perform batch operations or data capture on an e-commerce platform, by using a combination of Software routers and Proxies IP, you can easily automate the following tasks:
1. Create and manage multiple accounts in bulk:
Conclusion
To summarize, the combination of Software router and Proxies IP provides users with great flexibility and privacy protection. Whether you are conducting e-commerce operations, social media management, or data crawling and market analysis, this solution can significantly improve your operational efficiency and reduce risks.
Overall, by utilizing a combination of Software routers and Proxies IP, you can do all kinds of network operations more easily, protect your privacy, and improve your work efficiency at the same time.
0 notes
Text
#proxies#proxy#proxyserver#residential proxy#vpn#api#api testing services#automation#technews#software#innovation
0 notes
Text
4G Proxy vs. Residential Proxy: Which Suits Your Needs?

In today's rapidly evolving digital landscape, proxy servers have become indispensable tools for individuals and businesses alike. Whether you need enhanced online privacy, access to geo-restricted content, or want to protect yourself from cyber threats, proxies can help. Two popular options are 4G proxies and residential proxies. In this article, we will compare and contrast these two proxy types to help you determine which one suits your needs better.
What are 4G Proxies?
4G proxies are proxies that route your internet traffic through mobile devices connected to 4G networks. These proxies offer high speed, reliable connections, and are ideal for tasks that require dynamic IP addresses, such as web scraping, social media management, and sneaker purchasing.
Understanding Residential Proxies: Residential proxies, on the other hand, are IP addresses provided by internet service providers (ISPs) to homeowners. These proxies give you the ability to browse the internet anonymously, bypass geo-restrictions, and emulate genuine residential connections. They are well-suited for tasks requiring residential IP addresses, including ad verification and market research.
Pros and Cons of 4G Proxies:
Pros:
Fast and reliable connections.
Dynamic IP addresses.
Effective for high-demand tasks.
Ideal for social media management and automation.
Cons:
Higher cost compared to residential proxies.
Limited number of available IPs.
Can be more easily detected by anti-bot systems.
Pros and Cons of Residential Proxies:
Pros:
Authentic residential IP addresses.
Wider range of available IPs.
Less likely to be blocked by websites.
Suitable for tasks requiring diverse geographic locations
Cons:
Slower speeds compared to 4G proxies.
Potentially higher latency.
Less cost-effective for high-demand tasks.
Factors to Consider: To choose between 4G proxies and residential proxies, consider the following factors:
Specific use case requirements.
Budget and cost-effectiveness.
Desired connection speed and reliability.
IP diversity and availability.
FAQ:
Q1. Can 4G proxies be used for anonymous browsing?
A1. While 4G proxies can provide some level of anonymity, they are primarily designed for specialized tasks like web scraping and automation.
Q2. Are residential proxies suitable for high-demand tasks?
Residential proxies are generally better suited for tasks that require diverse IP addresses or need to emulate genuine residential connections rather than high-demand tasks.
Tips for Choosing the Right Proxy:
Identify your specific needs and goals.
Consider the budget and cost-effectiveness.
Evaluate the connection speed and reliability required for your tasks.
Assess the IP diversity and availability based on your use case.
Advices for Proxy Usage:
Test different providers before committing to one
Stay updated with the latest features and emerging technologies in the proxy industry.
Adhere to the terms of service and usage policies of your chosen proxy provider.
Keep in mind the ethical use of proxies and respect website policies.
'''Conclusion:'''
Both 4G proxies and residential proxies offer unique advantages and cater to different use cases. While 4G proxies excel in providing high-speed connections and dynamic IP addresses for specialized tasks, residential proxies offer authentic residential IPs and better compatibility with various websites. By considering your specific requirements and the pros and cons outlined in this article, you can make an informed decision on which proxy type suits your needs best.
0 notes
Photo

What Software Patterns (or Design Patterns) are and an introduction to the most common one
This is a short preview of the article: Software patterns, often referred to as design patterns, are a reusable and generalizable solution to a common problem that software developers face when designing and building software applications. Design patterns are essentially templates or blueprints for solving recurring design problems in
If you like it consider checking out the full version of the post at: What Software Patterns (or Design Patterns) are and an introduction to the most common one
If you are looking for ideas for tweet or re-blog this post you may want to consider the following hashtags:
Hashtags: #Adapter, #ClassDiagram, #ComputerScience, #DesignPatterns, #Facade, #Observer, #Proxy, #SoftwareArchitecture, #SoftwareEngineering, #SoftwarePatterns, #UML, #UMLDiagram
The Hashtags of the Categories are: #Java, #Programming, #Python, #SoftwareEngineering
What Software Patterns (or Design Patterns) are and an introduction to the most common one is available at the following link: https://francescolelli.info/software-engineering/what-software-patterns-or-design-patterns-are-and-an-introduction-to-the-most-common-one/ You will find more information, stories, examples, data, opinions and scientific papers as part of a collection of articles about Information Management, Computer Science, Economics, Finance and More.
The title of the full article is: What Software Patterns (or Design Patterns) are and an introduction to the most common one
It belong to the following categories: Java, Programming, Python, Software Engineering
The most relevant keywords are: adapter, Class diagram, computer science, Design Patterns, facade, observer, Proxy, software architecture, software engineering, Software Patterns, UML, UML diagram
It has been published by Francesco Lelli at Francesco Lelli a blog about Information Management, Computer Science, Finance, Economics and nearby ideas and opinions
Software patterns, often referred to as design patterns, are a reusable and generalizable solution to a common problem that software developers face when designing and building software applications. Design patterns are essentially templates or blueprints for solving recurring design problems in
Hope you will find it interesting and that it will help you in your journey
Software patterns, often referred to as design patterns, are a reusable and generalizable solution to a common problem that software developers face when designing and building software applications. Design patterns are essentially templates or blueprints for solving recurring design problems in a systematic and efficient way. Design patterns serve several important purposes in software development:…
#adapter#Class diagram#computer science#Design Patterns#facade#observer#Proxy#software architecture#software engineering#Software Patterns#UML#UML diagram
1 note
·
View note
Text
How To Smoothly Edit 4K Video On Slow Pc/Computer Without Lag: 2 pro tips
How To Smoothly Edit 4K Video On Slow Pc/Computer Without Lag: 2 pro tips. If you have a superfast computer then u can edit videos easyly with any software.BUt waht if ?you have slow computer or a low end pc and you still want to edit the 4k videos smoothly? in this video i have show you how to edit 4k or higher resolution video on a slow computer, i have showed you 2 differnt tips and tricks to edit vieo on any computer.The software i'm using here #filmora and #camtasia.

#desktop#editing#high resolution video edit#proxy#4k video editing#camtasia#filmora#video edit on slow pc#how to edit 4k video on slow computer#edit hd video on slow pc#edit 4k on filmora#how to speedup video editing software#easy tips#speed up tricks#low end pc#how to edit video on pc#smoothly edit#how to edit without lag
1 note
·
View note
Text
The Best Shared Proxies in 2023
Dedicated or residential IPs can be costly and are often unnecessary. Proxy services a shared data center provides are an affordable option for unprotected websites. Address changes may be made automatically by some service providers. They sell cheap shared proxies. These are some of the top shared Proxies.
The Best Shared Proxies in 2023
1) Smartproxy
Residential proxies are Smartproxy's specialty, but it also sells shared datacenter IPs. The company lets clients buy a plan for a specified number of IPs and bandwidth or just traffic.
You can receive 100,000 US and European traffic-based IPs or IP-based proxies from eight countries on four continents.
All services offer the whole IP pool and rotate proxies, making them ideal for site scraping. Smartproxy has excellent customer assistance and integration instructions, so you won't be alone.
30-minute sticky sessions may need to be longer for everyone.
Features:
Rotating proxy pool every request or 30 mins HTTP(S) protocols Five in the US and Europe (traffic-based), eight in four continents (IP-based). Bonus: 24/7 live assistance Price: $30/50 GB ($0.7/GB) or $10/100 IPs ($0.1/IP). A 3-day refund is possible.
2) Oxylabs
Oxylabs offers 15 US, European, and Asian shared proxies. The proxies have 29,00 addresses and can rotate with every connection request or form sticky sessions. Using the same session ID and IP address has no time limit. Start utilizing the service rapidly, and the dashboard provides traffic spending graphs.
Web scraping is robust, with good targeting possibilities but a high starting price.
Features:
Rotating proxy pool (every request, sticky sessions) Protocols: HTTP Locations: 15 Bonus: 24/7 live assistance From $50/77GB ($0.65/GB). 3-day refund for individuals, a 7-day trial for corporations
3) Bright Data
Bright Data offers shared proxies from a list of IPs or 20,000 addresses. Option 2 randomly selects IPs from Bright Data's 80 sites. Bright Data's robust proxy manager lets you rotate, filter, and control proxies.
You can pay monthly or as you go. In conclusion, Bright Data provides a complex and technological solution for experts. Those who are one will find Bright Data empowering; others may find it too complicated.
Features:
Shared IP list or rotating proxy pool (customizable rotation) HTTP(S) and SOCKS5 protocols Locations: over 100 24/7 live assistance, proxy manager, Price: Flexible and add-on-dependent. Pay as you go from $0.110/GB+$0.80/IP or subscribe from $500 ($0.094/GB + $0.68/IP). 3-day refund for individuals, a 7-day trial for corporations.
CONTINUE READING...
1 note
·
View note
Text
Differences between VMLogin and the Browser in the Virtual Machine @Vmlogin
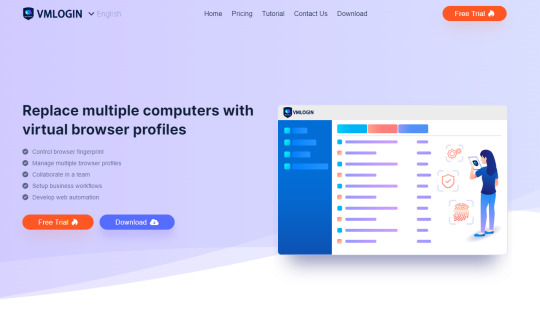
Virtual Machine (VM) means a complete computer system with full hardware system functionality simulated by software and running in a completely isolated environment.
Fingerprint Browser, also known as Anti-detect Browser. Simply put, it allows the operation and management of multiple platforms and accounts on the same electrical device, with no association between accounts. This anti-association concept is mainly used in e-commerce, social media marketing, affiliate marketing, web crawlers, and other businesses.
They both have similar functions by and large.
However, the fingerprint browser has better anti-detection and anti-association effects than the virtual machine, better privacy, and more information data will be more secure. And it is more suitable for users with multi-account business needs like professional e-commerce. Overall use is more stable.
So what is the difference between VMLogin Antidetect Browser and the browser in the virtual machine?
1. First of all, VMLogin is designed to replace the traditional virtual machine model with enhanced hardware fingerprint customization and emulation, because different virtual machines under the same host may have the same hardware fingerprint, only that the user cannot distinguish it.
2. VMLogin fingerprint is independent and unique for each browser.
3. Users can use it with a proxy IP to perfectly emulate the local browser environment anywhere in the world.
#vmlogin#dataprotection#software#incognito#virtualbrowser#secured#virtualplatform#searchsafely#protection#VM#social marketing#proxy#tiktok affiliate marketing#ecommerce#onlinebusiness#amazon#ebaybusiness#facebookads#twitter#threads#tumbler#antidetect browser#browser
0 notes
Text

Pentagon’s Pizza Index has accurately predicted 21 global crises since 1983
As tensions rise in the Middle East, a curious, crowd-driven theory known as the “Pentagon Pizza Index” has caught fire online.
On June 12 and 13, users on X (formerly Twitter) reported a sudden spike in pizza deliveries near the Pentagon and Department of Defense in Washington, D.C., sparking speculation that the United States may be quietly entering crisis mode behind closed doors.
The timing? Just hours before Israel reportedly struck targets in Iran in response to Tehran’s earlier drone and missile attacks. And once again, pizza orders were booming.
Cold war roots of the pizza theory. What began as a Soviet spy trick is now a digital-age meme
The idea isn’t new. During the Cold War, Soviet operatives observed pizza delivery activity in Washington, believing it signalled crisis preparation inside U.S. intelligence circles. They coined it “Pizzint” — short for pizza intelligence.
This tactic entered public lore on 1 August 1990, when Frank Meeks, a Domino’s franchisee in Washington, noticed a sudden surge in deliveries to CIA buildings. The next day, Iraq invaded Kuwait. Meeks later told the Los Angeles Times he saw a similar pattern in December 1998 during the impeachment hearings of President Bill Clinton.

As former CNN Pentagon correspondent Wolf Blitzer once joked in 1990, “Bottom line for journalists: Always monitor the pizzas.”
WWIII warning: What is the Pentagon Pizza Index today? A meme, an OSINT tool, or a symptom of digital-age paranoia?
The modern Pentagon Pizza Index is tracked through open-source intelligence (OSINT) tools. These include Google Maps, which shows real-time restaurant activity, and social media observations. Pages like @PenPizzaReport on X have dedicated themselves to watching for abnormal patterns.
On 1 June 2025, the account posted, “With less than an hour to go before closing time, the Domino’s closest to the Pentagon is experiencing unusually high footfall.”
A few hours later, reports emerged of a fresh escalation between Israel and Iran. For believers in the theory, it was yet another sign that something bigger was underway.
The April 2024 pizza spike. A recent example that reignited interest
The most notable recent instance occurred on 13 April 2024, the night Iran launched a massive drone and missile strike against Israel. That same evening, screenshots from delivery platforms showed pizzerias around the Pentagon, White House, and Department of Defense tagged as “busier than usual.”

Multiple Papa John’s and Domino’s branches reported increased orders. The correlation prompted viral memes and renewed interest in the theory.
According to Euro News, a user on X posted on 13 June 2025, “The Pentagon Pizza Index is hiking.”
Inside the logic: Why pizza? Food, fatigue and national security
The concept is deceptively simple. When military staff face a national emergency, they work longer shifts and can’t leave their posts. They need quick, filling food — and pizza fits the bill.
Studies in behavioural psychology show that under stress, people prefer calorie-dense, familiar comfort foods. During high-alert operations, officials may work 16–20 hour days. That creates a visible consumption spike that outsiders can track.
And because platforms like Google and Uber Eats share real-time data on restaurant activity, amateur analysts can monitor these patterns — no hacking required.
World War III: Pizza as a proxy for preparedness. It’s not perfect, but it’s consistent
The Pentagon Pizza Index isn’t a foolproof system. It could easily be triggered by something mundane: a long staff meeting, a software glitch, or a nearby college football game.
That’s why modern OSINT analysts often cross-reference pizza spikes with other indicators — like unusual aircraft movements, ride-hailing activity, or power usage near government buildings. When multiple signs align, it suggests more than coincidence.
As a senior analyst put it: “You can’t bank a war call on a pizza. But if the Pentagon’s burning the midnight oil and feeding everyone, it’s worth a second look.”
Official silence, public curiosity. What the US government says — and doesn’t say
Despite the chatter online, the US government has made no mention of pizza deliveries as indicators of crisis.
Responding to speculation about American involvement in Israel’s airstrikes on Iran, Republican Senator Marco Rubio said:
“We are not involved in strikes against Iran, and our top priority is protecting American forces in the region. Israel advised us that they believe this action was necessary for its self-defence.”
Still, the Pentagon’s silence on the pizza theory hasn’t stopped internet users from speculating.
Humour meets anxiety in the age of digital vigilance
In an age where open-source tools let ordinary people track the movement of jets, ships, and even pizzas, the Pentagon Pizza Index sits at the bizarre intersection of humour and fear. It turns snack food into a warning system.
It’s also a reminder: not all intelligence requires a badge. Sometimes, the clue might be just down the road — in a Domino’s queue.
Whether you see it as absurd or insightful, one thing is clear: when the pizzas fly, people pay attention.
Daily inspiration. Discover more photos at Just for Books…?
75 notes
·
View notes
Text

✦ the coffin dwellers gift to thee ~

✦ ── Computer themed , System alt terms
001 ── 'System' ; Computer , Network ノ Net , Code , Matrix , Motem , Motherboard¹ , CPU , Cache , Hardware¹ , Database ノ Datacenter , Hardrive ノ Drive , Domain , Server , Brower , Cloud , Index , Local area network ノ LAN , Operating system ノ OS , Sort field , Zipfile , Mainframe , Peripheral , Console , Terminal
002 ── 'Alters' ; Floppydisks ノ Disks , CDs , Robots ノ Bots² , Scripts , Facets , Wires , Bytes , Cookies , Ports , Software , Proxies , Clients , Users , Profiles , Files , Drives , Players , Accounts ノ Account holders , Add-ons , DLCs , Skins , Hackers , Developers ノ Devs
003 ── ¹ May also be used for body , ² May be reminiscent for those who have been called bots for using proxies on discord.

#❝ 🩸 ❞ — resurrection#plural#system stuff#plural community#plural id#plural flag#plural coining#system terms#system flag#did osdd#did system#dissociative system#osdd system#plural system#sysblr#system coining#system name#system names#system term#alter term#alter terms#system alt terms#system npts
357 notes
·
View notes
Text
Elon Musk’s minions—from trusted sidekicks to random college students and former Musk company interns—have taken over the General Services Administration, a critical government agency that manages federal offices and technology. Already, the team is attempting to use White House security credentials to gain unusual access to GSA tech, deploying a suite of new AI software, and recreating the office in X’s image, according to leaked documents obtained by WIRED.
Some of the same people who helped Musk take over Twitter more than two years ago are now registered as official GSA employees. Nicole Hollander, who slept in Twitter HQ as an unofficial member of Musk’s transition team, has high-level agency access and an official government email address, according to documents viewed by WIRED. Hollander’s husband, Steve Davis, also slept in the office. He has now taken on a leading role in Musk’s Department of Government Efficiency (DOGE). Thomas Shedd, the recently installed director of the Technology Transformation Services within GSA, worked as a software engineer at Tesla for eight years. Edward Coristine, who previously interned at Neuralink, has been onboarded along with Ethan Shaotran, a Harvard senior who is developing his own OpenAI-backed scheduling assistant and participated in an xAI hackathon.
“I believe these people do not want to help the federal government provide services to the American people,” says a current GSA employee who asked not to be named, citing fears of retaliation. “They are acting like this is a takeover of a tech company.”
The team appears to be carrying out Musk’s agenda: slashing the federal government as quickly as possible. They’re currently targeting a 50 percent reduction in spending for every office managed by the GSA, according to documents obtained by WIRED.
There also appears to be an effort to use IT credentials from the Executive Office of the President to access GSA laptops and internal GSA infrastructure. Typically, access to agency systems requires workers to be employed at such agencies, sources say. While Musk's team could be trying to obtain better laptops and equipment from GSA, sources fear that the mandate laid out in the DOGE executive order would grant the body broad access to GSA systems and data. That includes sensitive procurement data, data internal to all the systems and services GSA offers, and internal monitoring software to surveil GSA employees as part of normal auditing and security processes.
The access could give Musk’s proxies the ability to remote into laptops, listen in on meetings, read emails, among many other things, a former Biden official told WIRED on Friday.
“Granting DOGE staff, many of whom aren't government employees, unfettered access to internal government systems and sensitive data poses a huge security risk to the federal government and to the American public,” the Biden official said. “Not only will DOGE be able to review procurement-sensitive information about major government contracts, it'll also be able to actively surveil government employees.”
The new GSA leadership team has prioritized downsizing the GSA’s real estate portfolio, canceling convenience contracts, and rolling out AI tools for use by the federal government, according to internal documents and interviews with sources familiar with the situation. At a GSA office in Washington, DC, earlier this week, there were three items written on a white board sitting in a large, vacant room. “Spending Cuts $585 m, Regulations Removed, 15, Square feet sold/terminated 203,000 sf,” it read, according to a photo viewed by WIRED. There’s no note of who wrote the message, but it appears to be a tracker of cuts made or proposed by the team.
“We notified the commercial real estate market that two GSA properties would soon be listed for sale, and we terminated three leases,” Stephen Ehikian, the newly appointed GSA acting administrator, said in an email to GSA staff on Tuesday, confirming the agency’s focus on lowering real estate costs. “This is our first step in right-sizing the real estate portfolio.”
The proposed changes extend even inside the physical spaces at the GSA offices. Hollander has requested multiple “resting rooms,” for use by the A-suite, a team of employees affiliated with the GSA administrator’s office.
On January 29, a working group of high-ranking GSA employees, including the deputy general counsel and the chief administrative services officer, met to discuss building a resting room prototype. The team mapped out how to get the necessary funding and waivers to build resting rooms in the office, according to an agenda viewed by WIRED.
After Musk bought Twitter, Hollander and Davis moved into the office with their newborn baby. Hollander helped oversee real estate and office design—including the installation of hotel rooms at Twitter HQ, according to a lawsuit later filed by Twitter executives. During the installation process, one of the executives emailed to say that the plans for the rooms were likely not code compliant. Hollander “visited him in person and emphatically instructed him to never put anything about the project in writing again,” the lawsuit alleged. Employees were allegedly instructed to call the hotel rooms “sleeping rooms” and to say they were just for taking naps.
Hollander has also requested access to Public Buildings Service applications; PBS owns and leases office space to government agencies. The timing of the access request lines up with Ehikian’s announcement about shrinking GSA’s real estate cost.
Musk’s lieutenants are also working to authorize the use of AI tools, including Google Gemini and Cursor (an AI coding assistant), for federal workers. On January 30, the group met with Google to discuss Telemetry, a software used to monitor the health and performance of applications, according to a document obtained by WIRED.
A-suite engineers, including Coristine and Shaotran, have requested access to a variety of GSA records, including nearly 10 years of accounting data, as well as detailed records on vendor payments, purchase orders, and revenue.
The GSA takeover mimics Musk’s strategy at other federal agencies like the Office of Personnel Management (OPM). Earlier this month, Amanda Scales, who worked in talent at Musk’s xAI, was appointed as OPM chief of staff. Riccardo Biasini, former Tesla engineer and director of operations at the Boring company, is now a senior adviser to the director. Earlier this week, Musk cohorts at the US Office of Personnel Management emailed more than 2 million federal workers offering “deferred resignations,” allegedly promising employees their regular pay and benefits through September 30.
The email closely mirrored the “extremely hardcore” note Musk sent to Twitter staff in November 2022, shortly after buying the company.
Many federal workers thought the email was fake—as with Twitter, it seemed designed to force people to leave, slashing headcount costs without the headache of an official layoff.
Ehikian followed up with a note to staff stressing that the email was legitimate. “Yes, the OPM email is real and should be taken very seriously,” he said in an email obtained by WIRED. He added that employees should expect a “further consolidation of offices and centralization of functions.”
On Thursday night, GSA workers received a third email related to the resignation request called “Fork in the Road FAQs.” The email explained that employees who resign from their positions would not be required to work and could get a second job. “We encourage you to find a job in the private sector as soon as you would like to do so,” it read. “The way to greater American prosperity is encouraging people to move from lower productivity jobs in the public sector to higher productivity jobs in the private sector.”
The third question posed in the FAQ asked, “Will I really get my full pay and benefits during the entire period through September 30, even if I get a second job?”
“Yes,” the answer read. “You will also accrue further personal leave days, vacation days, etc. and be paid out for unused leave at your final resignation date.”
However, multiple GSA employees have told WIRED that they are refusing to resign, especially after the American Federation of Government Employees (AFGE) told its members on Tuesday that the offer could be void.
“There is not yet any evidence the administration can or will uphold its end of the bargain, that Congress will go along with this unilateral massive restructuring, or that appropriated funds can be used this way, among other issues that have been raised,” the union said in a notice.
There is also concern that, under Musk’s influence, the federal government might not pay for the duration of the deferred resignation period. Thousands of Twitter employees have sued Musk alleging that he failed to pay their agreed upon severance. Last year, one class action suit was dismissed in Musk’s favor.
In an internal video viewed by WIRED, Ehikian reiterated that GSA employees had the “opportunity to participate in a deferred resignation program,” per the email sent by OPM on January 28. Pressing his hands into the namaste gesture, Ehikian added, “If you choose to participate, I offer you my heartfelt gratitude for your service to this nation. If you choose to stay at the GSA, we’ll work together to implement the four pillars from the OPM memo.” He ended the video by saying thank you and pressing his hands into namaste again.
52 notes
·
View notes